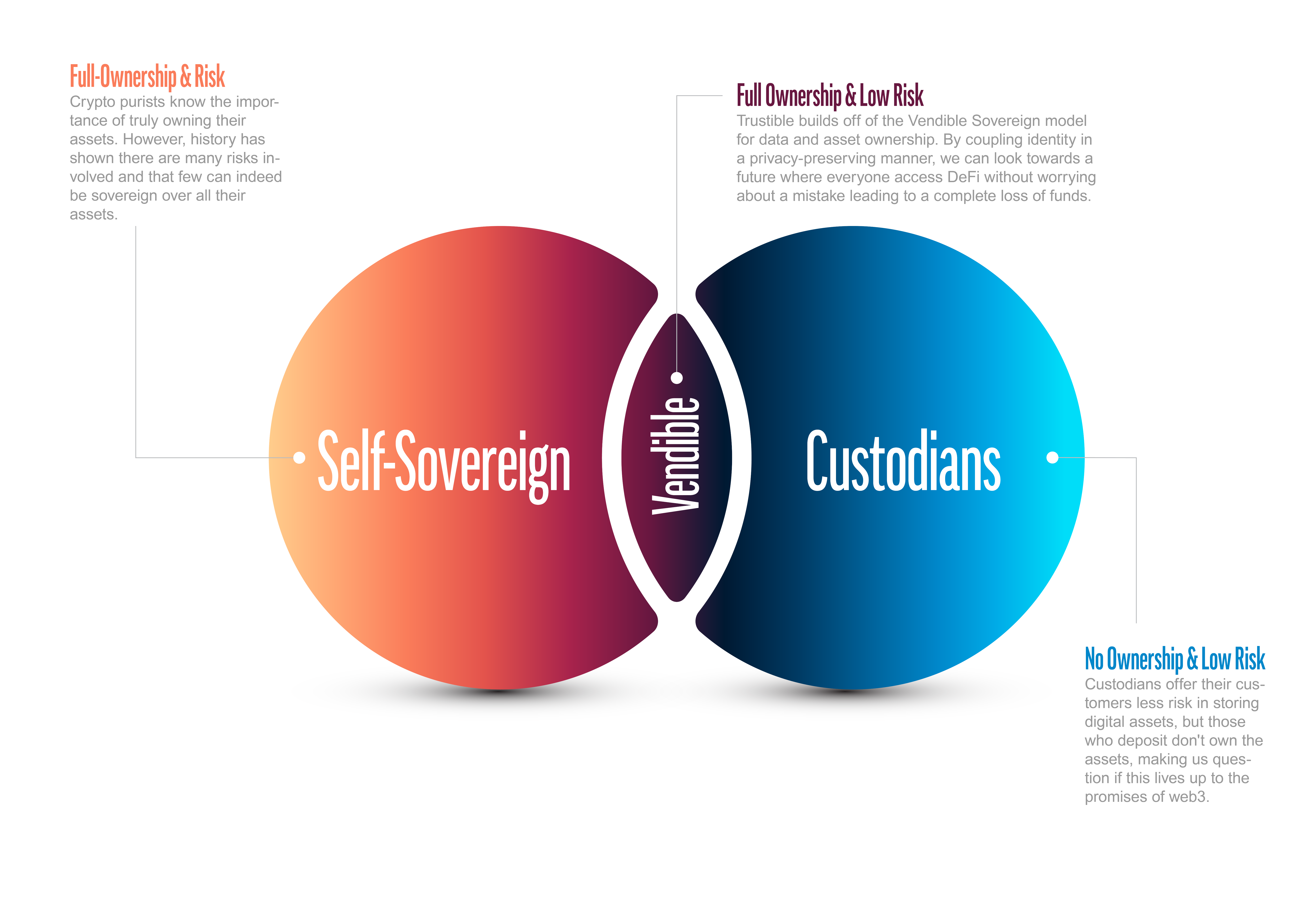
Tackling the biggest roadblock to widespread DeFi adoption








We've seen the headlines
We've felt the fear each time we write down that seed phrase. Each time we store it somewhere safe but wonder...what if...